Securing IoT devices with open-source hardware and software
Our colleagues Sebastian Haas and Nils Asmussen have published a guest article in HiPEAC Magazine:
We rely on smart systems and devices every day, most of which are connected via the internet. Their network forms the internet of things (IoT), which is becoming increasingly integrated into our everyday lives. These IoT devices must not only meet performance and energy-consumption requirements; at a time when attacks and data breaches are hitting the news almost daily, strong security and privacy properties are equally important. Providing these security and privacy properties requires not only addressing software problems, but also hardware vulnerabilities like Meltdown and Spectre, as recent years have shown.
Traditional multiprocessor architectures in IoT devices allow a modular system design and easy integration of different components into one system. However, hardware components are typically insufficiently isolated from each other. For example, an attacker with network access to the IoT device may exploit software and hardware bugs in a single component to get access to all other components in the system. This allows the attacker to manipulate the system or leak confidential data. In other words, the attacker can compromise the whole device.
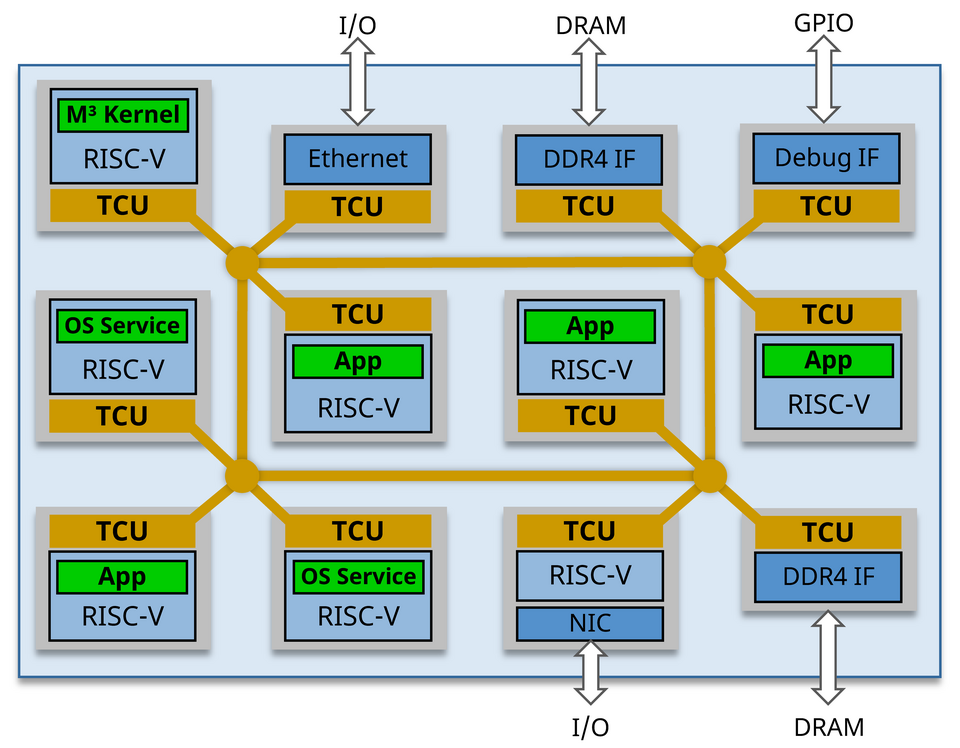
The Barkhausen Institut is developing an open-source hardware/software co-design, called M³, that addresses security requirements at the hardware, operating system, and application level. On the hardware side, M³ builds upon a tiled hardware architecture with physically separated tiles and a custom per-tile hardware component for cross-tile communication. This hardware component is called the trusted communication unit (TCU) which isolates tiles from each other and selectively allows communication.
The current hardware platform consists of multiple heterogeneous tiles which are connected by a network-on-chip. Tiles include open-source RISC-V Rocket cores or interfaces to input/output (I/O) peripherals and off-chip memory. The hardware platform is available as open-source, which includes hardware register transfer level (RTL) code and a tool flow to compile and run the design on a field-programmable gate array (FPGA).
On the software side, M³ provides a microkernel-based operating system which is also available as open source. The microkernel runs on a dedicated ‘kernel tile’, whereas operating-system services (e.g. file systems and network stacks) and applications run on the remaining ‘user tiles’. By default, all tiles are isolated from each other and only the kernel tile can establish communication channels between tiles. The microkernel is therefore programming the TCUs to enforce a desired security policy. For example, an application can access the file system only if permitted by the microkernel. This hardware/software co-design approach keeps malicious software and untrusted hardware components on the respective isolated tile and makes it much harder for an attacker to compromise the whole system.
Please have a look at the entire magazine here: https://www.hipeac.net/magazine/june/.
Further information:
M³ open-source hardware available on GitHub
github.com/Barkhausen-Institut/M3-hardware
M³ open-source software available on GitHub
github.com/Barkhausen-Institut/M3
Talk by Sebastian and Nils at Computing Systems Week Lyon
